
New Ransomware Forces People to be Charitable to Get Their Data Back
This ransomware was discovered by threat analysis firm , which identifies it as “global malware.
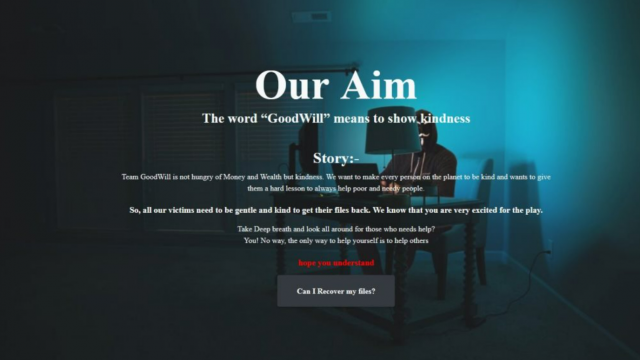
This screen lets you know you’ve been hit with the GoodWill ransomeware. (Image: CloudSEK)
The first stage of file recovery involves giving clothes and blankets to people on the side of the road. The instructions note people can die without adequate clothing. In order to satisfy the requirement, the victim must take video of the event. Then they have to post it to an Instagram, Facebook, or WhatsApp story using a photo frame provided by the hackers. They must also encourage others to do likewise. Finally, they have to screenshot the story and email it to the group in order to proceed to the next round.
The next phase is about feeding hungry children. The victim has to pick up five kids under the age of 13 and take them to dinner. This has to take place at a Dominos, KFC, or Pizza Hut. It’s not clear why an actual restaurant like Olive Garden was left off the list. It’s also not stated whether you must accompany them to the nearest bathroom afterwards. Once they’ve devoured some fast food the victim has to take selfies documenting their “happy faces.” Naturally, the selfies need to be made into a story for social media. They must also email the hackers a copy of the receipt and the requisite screenshots. After that’s verified, and you’ve returned said children to wherever you found them, it’s off to the final phase.
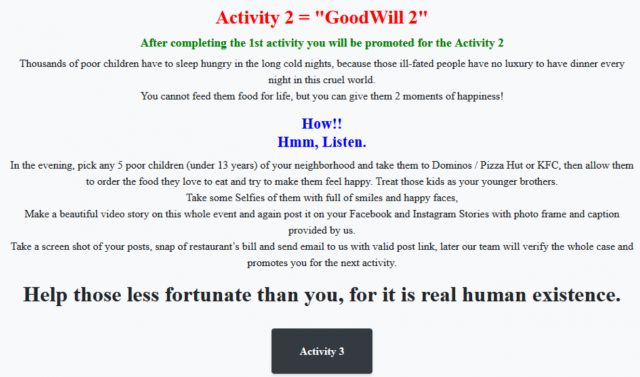
(Image: CloudSEK)
The third task is arguably the most difficult: you must pay someone’s hospital tab. In the United States, this could be a minefield since you never know what insurance will cover. It also seems like this would be something that’s impossible to figure out. However, the instructions say they should go to a hospital and start talking to people. Naturally they must record the conversation. This chat will include the victim telling them they don’t need to worry anymore. They are then instructed to pay the “maximum part of required amount.” To finish the phase, they must send the hackers the audio recording, but there’s no requirement to submit proof of payment. Finally, it’s time for the last social media post. This post summarizes the person’s transformation into a good Samaritan, all thanks to malware. Once all conditions are met, the victim receives a decryption kit and should be able to recover their data.
CloudSEK says it’s been able to trace the origins of this attack to a group in India. This was discovered through IP addresses and the language used in some of the code. Though GoodWill is different in nature to other ransomware attacks, mitigation efforts are the same. Always have a backup of important documents. In addition, make sure to test your backups to make sure they are working. Even better, regularly save image files of your installation to quickly restore your PC. Of course, regular PC habits apply as well, such as using two-factor authentication, not clicking on links in email, etc. Be careful, or you might end up at KFC, or worse, a hospital.
Now Read: