Researchers discover malware that records users’ screens when they watch porn
Researchers from antivirus developer ESET recently discovered a new form of spam-delivered malware that threatens to steal unsuspecting users’ passwords and financial information, and record their screens if they watch pornography.
The virus is called Varenyky and it’s a doozy. It’s apparently been designed to target customers of French ISP Orange SA, but the researchers indicate there’s nothing stopping someone from using the same malware on other ISPs or in other areas. It’s delivered via a very official looking email that appears to be a phone bill.
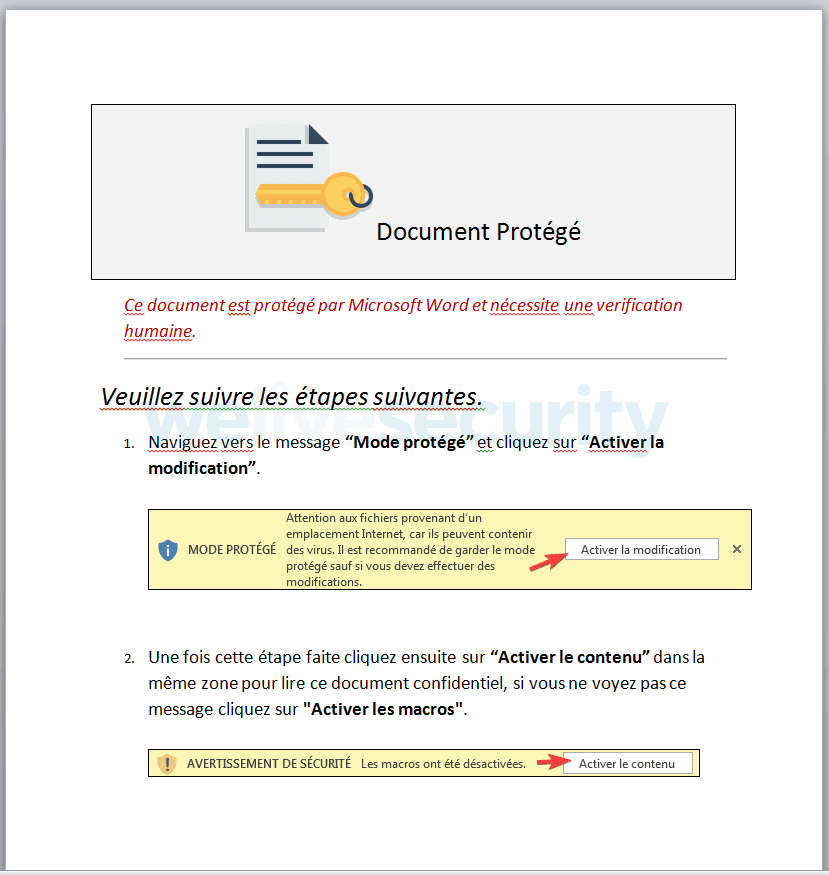
Unsuspecting victims believe they’re opening a document that’s been protected and secured by Microsoft, when in reality they’re activating the virus and giving it permission to run macros in Word. According to a post on ESET’s website:
Overall, the email text content, the document’s filename and the “protected” content of the document emphasize to the recipients that they are dealing with a real bill and that they should open it. The quality of the French is very good; overall, the document is convincing.
Once active, the macro contained in the fake bill executes processes that allows the malware to download the additional files it needs to gather passwords, propagate to other systems, and record your screen.
An English version of the email that victims would supposedly receive after their screens were recorded was posted earlier this year by ESET:
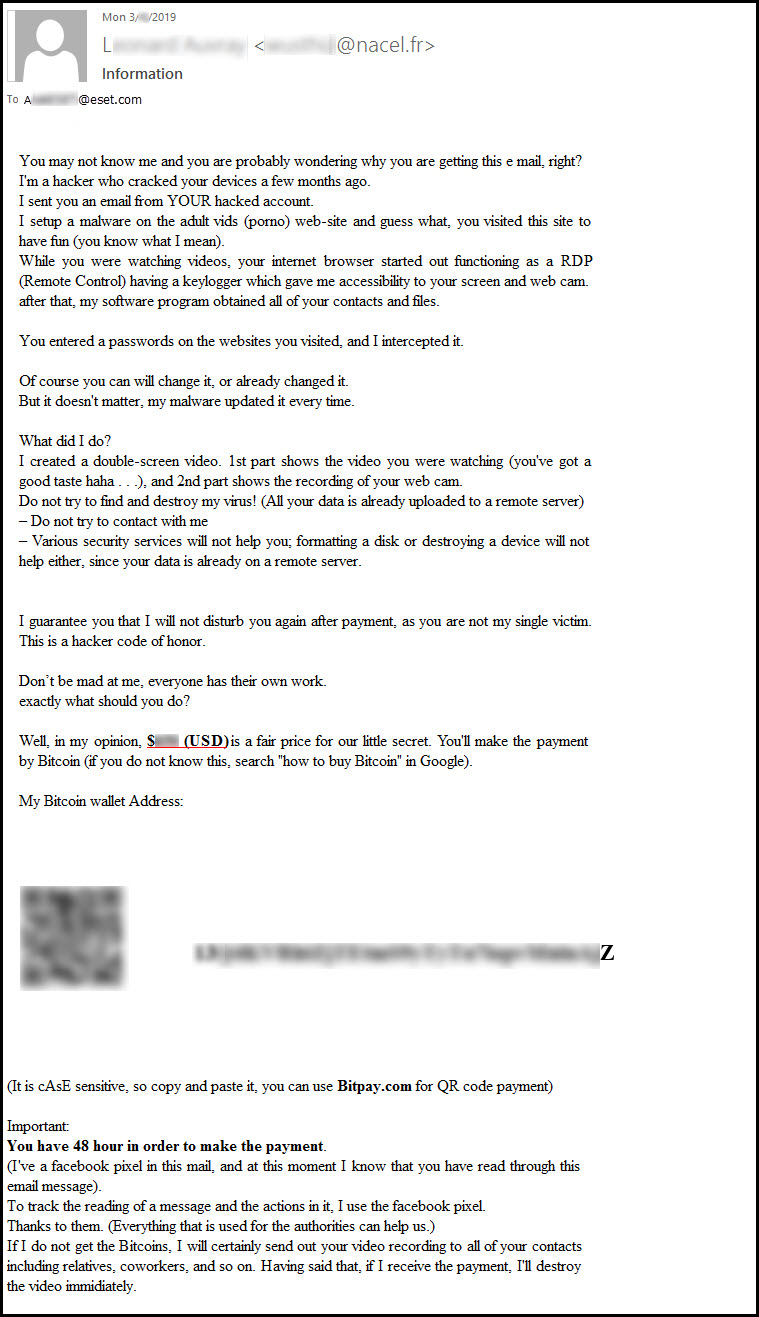
So how dangerous is it? The sextortion scam aspect of the malware doesn’t appear to be a major threat. ESET security expert Bruce P. Burrell said it’s likely the so-called hacker is using a “sextortion scam kit” they purchased on the dark web. To date, it doesn’t appear as though anyone’s been extorted by Varenyky in this method. But anyone who’s downloaded the fake bill and mistakenly given it permission to run macros is at very high risk of having their passwords and financial information stolen and spreading the malware to people in their contacts list.
While Varenyky doesn’t appear to be a global threat yet, and so far there’s been no documented instances of it successfully extorting anyone, the simplicity of its attack vector is noteworthy. And, according to ESET, the malware’s developers are tenacious:
Many functions have been added and then quickly removed across many different versions in a short period of time (two months). This shows that the operators are actively working on their botnet and are inclined to experiment with new features that could bring a better monetization of their work.
In the meantime, security experts say the best defense against malware is to keep your OS and antivirus software up to date, and avoid opening email attachments or downloading files unless you’re 100-percent certain they’re not dangerous.
Read next: This spooky Monero-mining malware waits to be controlled remotely